Fraud Types
How are fraud codes built?
The Evina fraud codes are made up of 4 digits.
First digit: Nature of sessions
1xxx: authentic
2xxx: fraudulent
3xxx: accidental
4xxx: errors
5xxx: bots
6xxx: Ad-hoc rule / custom codes
Second digit: fraud family
Example: 22xx: malicious apps / 24xx: spoofing
Third and fourth digits: type or generation in the family
1000 - No Fraud
No fraud has been detected.
21XX - Code Injection
Code numbers
-
- 2101
- 2102
Definition
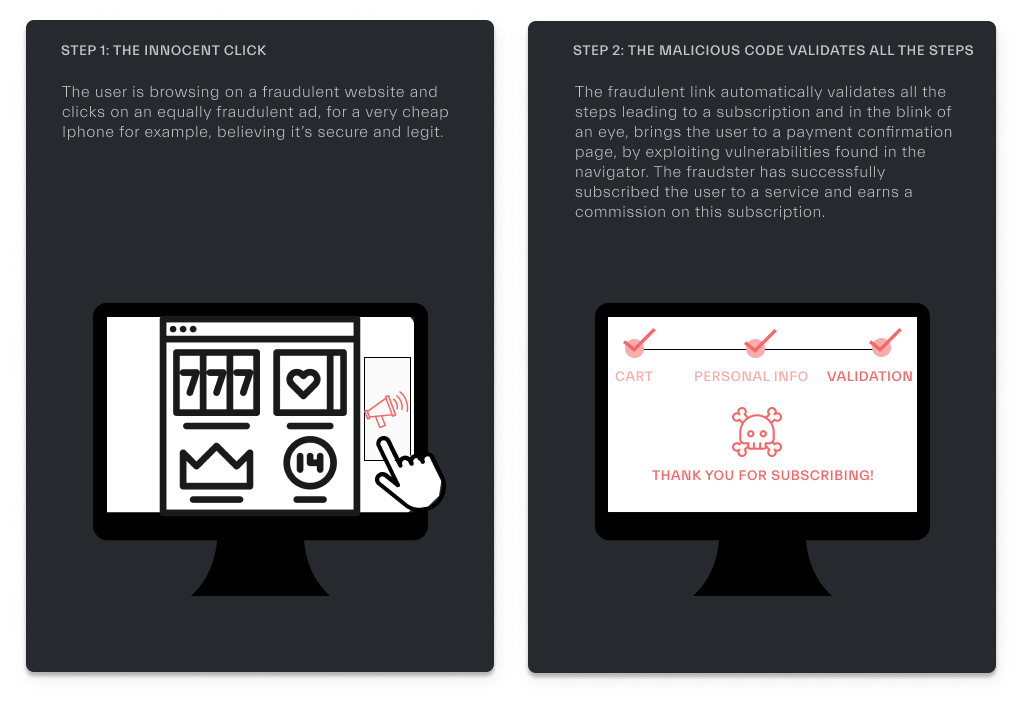
Hackers exploit a flaw in the browser or the server to inject malicious code to end users. The injection can be done in different places, i.e. header, URL, etc.
Real-life case scenario: You click on a link and all the steps of the payment flow are clicked upon automatically as shown below.
22XX - Malicious Apps
Code numbers
-
- 2201
- 2202 - AUG2018.
- 2203 - MAR2019.
- 2204 - APR2020.
- 2205 - JAN2021.
Definition
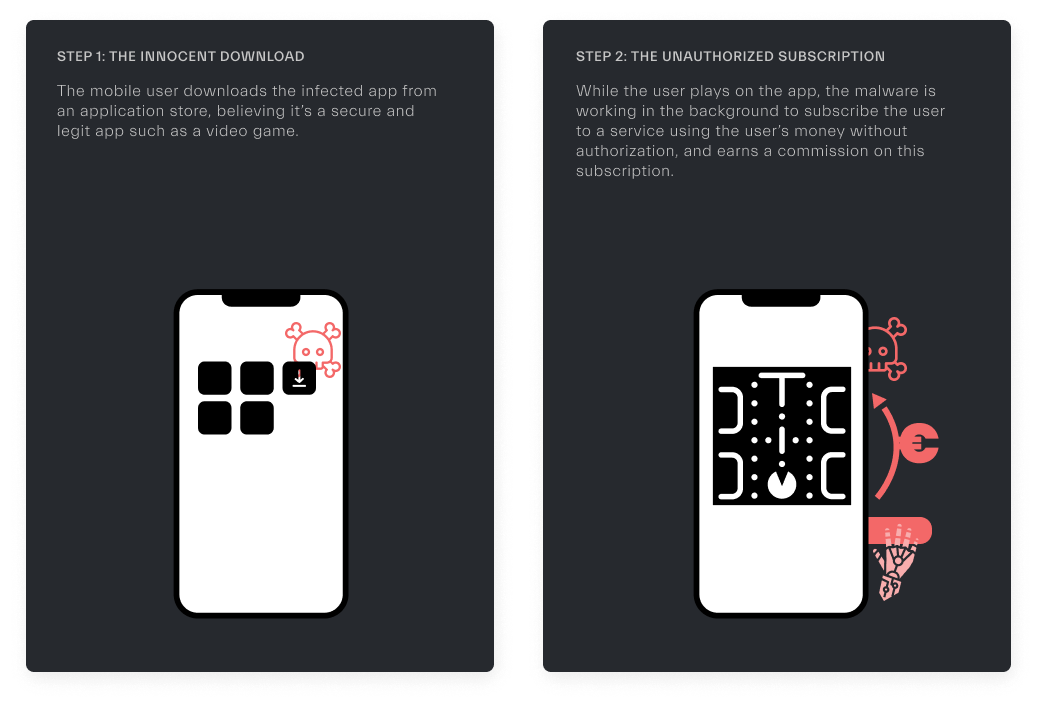
Application programmed to go through all the steps of the flow in place of the final user without notifying him.
Real-life case scenario: The user downloads an application on purpose, believing that it is a game and a subscription is processed in the background.
23XX - Clickjacking
Code numbers
-
- 2301
- 2302
Definition
The purpose of the hacker is to intercept the click, so the user believes that he has clicked on a specific button but in reality he did not, he has clicked somewhere else. In order to avoid any false positives, you should provide us with the URL of any iframe used in your flow.
Real-life case scenario: The payment page is transparent, and it is set up behind a page that is more interesting for the user, ie: funny kitten video.

24XX - Spoofing
Code numbers
-
- 2401
- 2402 - OCT2017
- 2403 - FEB2018
- 2404 - SEP2019.
- 2405 - APR2019.
- 2407- DEC2019.
- 2408 - APR2020.
- 2409 - APR2020
- 2410 - MAY2020.
- 2411 - MAY2020.
- 2412 - JUL2020.
- 2413 - JUL2020.
- 2414 - AUG2020.
- 2415 - SEP2020.
- 2416 - OCT2020.
- 2417 - OCT2020.
- 2418 - OCT2020.
- 2419 - OCT2020.
- 2420 - DEC2020.
- 2421 - JAN2021.
- 2422 - JAN2021.
- 2423 - FEB2021.
- 2424 - MAR2021.
- 2425 - MAY2021.
- 2426 - JUL2021.
- 2427 - SEP2021.
- 2428 - SEP2021.
- 2429 - JAN2022.
- 2430 - APR2022.
- 2431 - APR2022.
- 2432 - JUN2022.
Definition
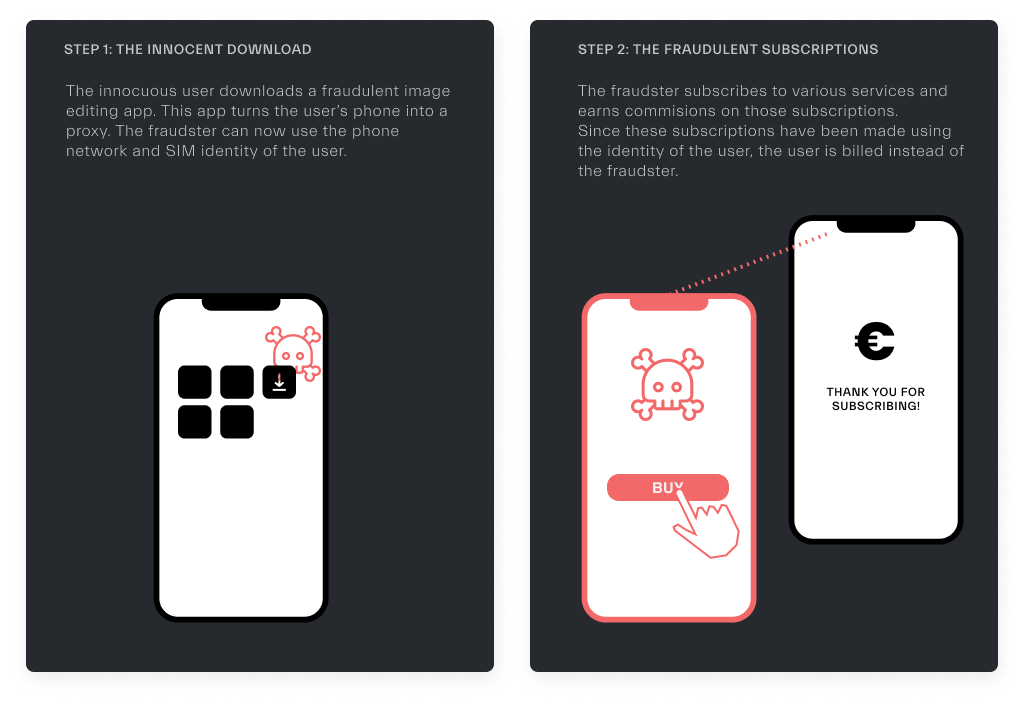
The purpose of the hacker is to steal/usurp the network/sim identity of the user to make a payment on his behalf. This can be done through a malicious app or PC malware connected to a mobile device.
Real-life case scenario: The user uses a free VPN, sharing his connection, which will be used by fraudsters to perform subscriptions from other devices.
25XX - Remotely Controlled Fraud
Code numbers
-
- 2501
- 2502 - AUG2018.
- 2503 - MAR2020.
- 2504 - MAY2020
- 2505 - JUN2020
- 2506 - SEP2020
- 2507 - DEC2020
- 2508 - JAN2021
- 2509 - MAR2021
- 2510 - MAR2021
- 2511 - MAR2021
- 2512 - APR2021
- 2513 - APR2021
- 2514 - APR2021
- 2515 - MAY2021
- 2516 - MAY2021
- 2517 - MAY2021
- 2518 - MAY2021
- 2519 - JUN2021
- 2520 - JUN2021
- 2521 - JUN2021
- 2522 - JUN2021
- 2523 - JUL2021
- 2524 - JUL2021
- 2525 - JUL2021
- 2526 - JUL2021
- 2527 - JUL2021
- 2528 - JUL2021
- 2529 - AUG2021
- 2530 - AUG2021
- 2531 - AUG2021
- 2532 - AUG2021
- 2533 - AUG2021
- 2534 - AUG2021
- 2535 - AUG2021
- 2536 - AUG2021
- 2537 - AUG2021
- 2538 - AUG2021
- 2539 - AUG2021
- 2540 - AUG2021
- 2541 - AUG2021
- 2542 - AUG2021
- 2543 - AUG2021
- 2544 - AUG2021
- 2545 - SEP2021
- 2546 - SEP2021
- 2547 - SEP2021
- 2548 - SEP2021
- 2549 - SEP2021
- 2550 - SEP2021
- 2551 - SEP2021
- 2552 - SEP2021
- 2553 - OCT2021
- 2554 - OCT2021
- 2555 - OCT2021
- 2556 - OCT2021
- 2557 - NOV2021
- 2558 - NOV2021
- 2559 - NOV2021
- 2560 - NOV2021
- 2561 - NOV2021
- 2562 - NOV2021
- 2563 - NOV2021
- 2564 - NOV2021
- 2565 - NOV2021
- 2566 - DEC2021
- 2567 - DEC2021
- 2568 - DEC2021
- 2569 - DEC2021
- 2569 - DEC2021
- 2570 - DEC2021
- 2571 - DEC2021
- 2572 - DEC2021
- 2573 - DEC2021
- 2574 - JAN2022
- 2575 - JAN2022
- 2576 - JAN2022
- 2577 - FEV2022
- 2578 - FEV2022
- 2579 - FEV2022
- 2580 - MAR2022
- 2581 - MAR2022
- 2582 - MAR2022
- 2583 - MAR2022
- 2584 - APR2022
- 2585 - APR2022
- 2586 - MAY2022
- 2587 - JUN2022
- 2588 - MAY2022
- 2589 - JULY2022
- 2590 - SEPT2022
- 2591 -SEPT2022
- 2592 - OCT2022
- 2593 - OCT2022
- 2594 - JAN2023
- 2595 - MAY2023
Definition
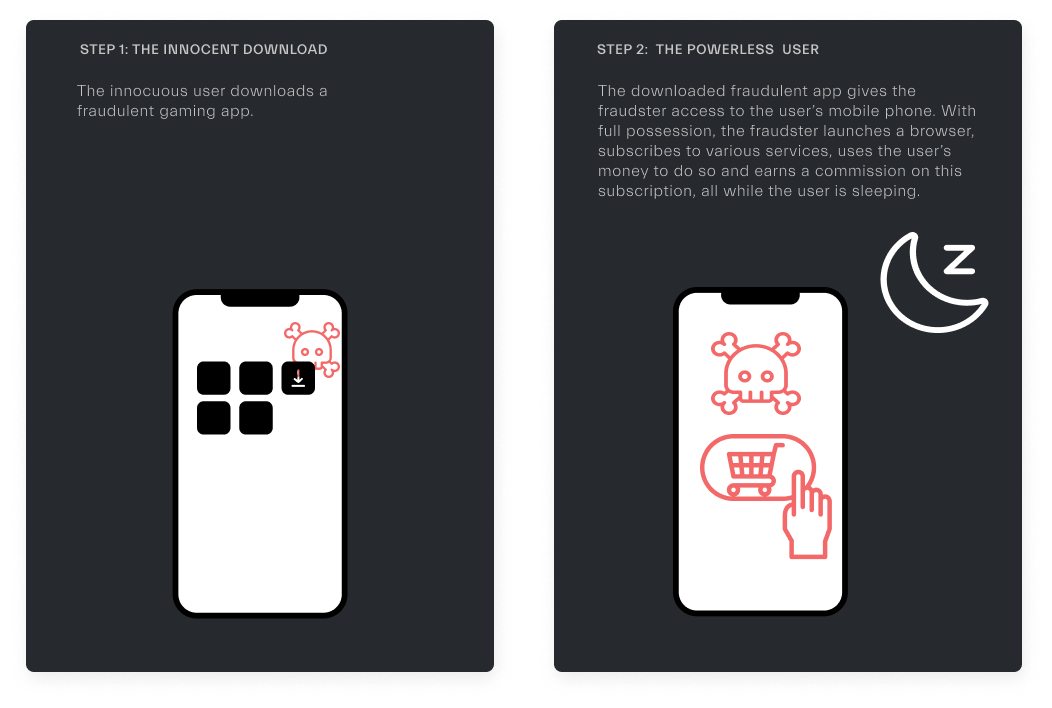
As its name suggests, a fraudster takes control of the device via malware to subscribe to services. The device is controlled by a program that emulates human behavior. This can be done through a malicious app, a PC malware connected to a mobile device, or through a monitoring tool.
Real-life case scenario: the user's phone is on the table and without touching it, the browser is launched and the purchase is made.
26XX - Blacklisted
Code numbers
-
- 2601 - Blacklist of the applications detected as fraudulent.
- 2602 - Blacklist of the domain names detected as fraudulent.
- 2603 - Blacklist of the suspicious behaviors from an application detected as fraudulent.
- 2604 - An abnormal behavior detected as fraudulent.
- 2605 - An abnormal behavior detected as fraudulent. Dec 2022.
Definition
Apps, domains, or behaviors that are disregarded because they are untrustworthy.
27XX - Replay Attack
Code numbers
-
- 2701
- 2702 - DEC19
- 2703 - JAN20
- 2704 - JUN21
Definition
A form of network attack in which a transmission is maliciously repeated or delayed by an attacker who has intercepted the transmission.
Real-life case scenario: Nothing is noticeable for the end user. Fraudsters tend to repeat the real end user flow.
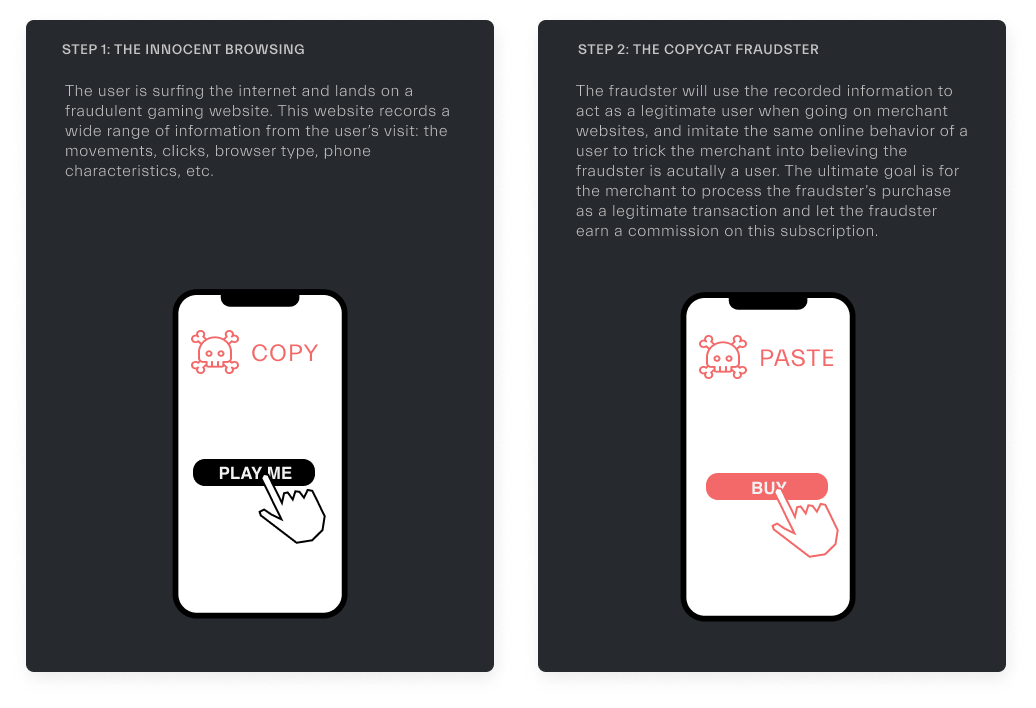
28XX - Bypass Fraud
Code numbers
- 2801 - Detection Type 1
- 2802 - Detection Type 2
- 2803 - Detection Type 3 - Crash Javascript
- 2804 - Detection Type 4
- 2805 - Detection Type 5
- 2806 - Detection Type 6 - New Fraud byPass June 2023
Definition
The fraudster deletes or blocks the anti-fraud script from the landing page hiding end users’ actions. He can also directly go to the URL post billing without making a click.
Real-life case scenario: The end user will “see” the page going directly from the landing page to the confirmation page.
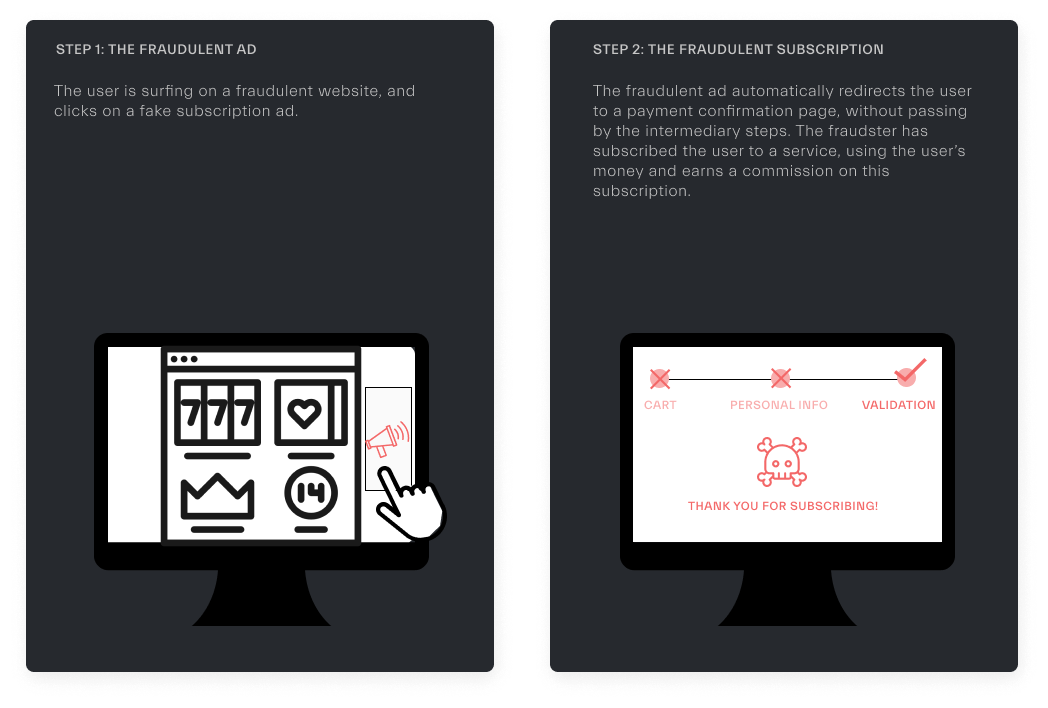
31XX - Accidental click
Code numbers
-
- 3101: Accidental click - caused by browser
- 3102: Accidental click - Pocket click
- 3103: Accidental click - Accidental movements on the page
- 3104: Accidental click - Accidental movements on the page - new metrics
- 3105: Accidental click -No mouvements detected
- 3106: Accidental click - Accidental movements on the page - new metrics
Definition
Click to be considered as an unintentional click. It can be caused by browser bugs, fat fingers or too many clicks on the page before the protected page.
4101 - Kit expired
Definition
A kit's lifespan is 48 hours. This code will be returned in the event of a user action made client-side after this delay.
4102 - Token expired
Definition
A token expires after 24 hours. If a call is made on a check with an expired token, this code is returned.
5101- Google Bot - 5102 - Others Crawlers/Bots
Definition
Flow made by a Google bot. Any Crawlers or others bots than Google.
5201 - Impersonator Bots
Definition
Bots that mimic human behavior type 1.
61XX - Ad-hoc rule
Definition
Rules that can be defined with our customers (ex: rules based on the number of purchase attempts, rules based on IP geolocation, etc.)
Code numbers
-
- 6101 - End user's IP country is not allowed
- 6102 - End user's IP origin is not allowed
- 6111 - This user made an attempt on the same service less than 1 minute ago
- 6112 - This user made an attempt on the same service less than 5 minutes ago
- 6113 - This user made an attempt on the same service less than 1 hour ago
- 6114 - This user made an attempt on the same service less than 24 hours ago
- 6121 - This user made an attempt on another service less than 1 minute ago
- 6122 - This user made an attempt on another service less than 5 minutes ago
- 6123 - This user made an attempt on another service less than 1 hour ago
- 6124 - This user made an attempt on another service less than 24 hours ago
- 6201 - Specific Legal Rules
- 6202 - Specific Customer Rules.
- 6203 - Specific Customer Rules.
- 6204 - Mobile Android devices with outdated and un-updatable operating systems pose a significant source of vulnerabilities.
- 6205 - Specific Rules for Proxy and VPN identification
- 6206 - UserId-based Multiple attempts
- 6207 - Lead generation attempt or aggressive campaign - level 1
- 6208 - Lead generation attempt or aggressive campaign - level 2
- 6209 - Lead generation attempt or aggressive campaign - level 3
Updated 4 months ago
